| Apply Now |
The Master program in Cyber Security aims at specialized training in Informatics Security (Cybersecurity). Giving response to a set of initiatives that have been developed at the National and International level, targeting the development of knowledge competencies in the field of Cybersecurity (e.g. IFC-UTICA Directive, US Cybersecurity Information Sharing Act, EU Directive for security across the Union) as a way to support the growth of the digital economy, preserving the privacy of citizens, and combat and prevent cybercrime and cyberterrorism, the master program has the following objectives:
It is expected that upon completion of the Master in Cyber Security students will have the following knowledge, skills, and competencies:
| Apply Now |
| Code | Course Title |
Credits |
|---|---|---|
| CS443 | Cryptography |
3 |
| CS412 | Cyber Security Assessment and Management | 3 |
| CS431 | AI for Cybersecurity | 4 |
| CS411 | Computer Network Security | 4 |
| ETH391 | Engineering Ethics & Professional Practice | 3 |
| CS432 | Incident Response and Recovery | 4 |
|
|
Total : | 21 |
| Code | Course Title |
Credits |
|---|---|---|
| CS495 | Machine Learning |
4 |
| CS508 | IoT Security |
4 |
| COM307 | Effective Technical Communication |
3 |
| CS453 | Pervasive Computing & Cloud |
4 |
| CS424 | Design and Development of Secure Software |
3 |
| ISS498 | EC-C Certification: CEH or NDE |
3 |
|
|
Total : | 21 |
| Code | Course Title |
Credits |
|---|---|---|
| CS504 |
Blockchain Technology |
3 |
| CS430
|
Informatics Security and Law |
4 |
| CS512 |
Security and Privacy |
4 |
| CS513 |
Information Technologies Security |
4 |
| ISS497
|
Research Methods |
3 |
| CS507 |
Digital Forensics + Certification |
3 |
| CS520
|
Security Auditing (Extra Class) |
3 |
|
|
Total : | 21 |
| Code | Course Title |
Credits |
|---|---|---|
| ISS599 |
Master Thesis |
21 |
Cryptography
This course covers practical aspects of cryptography, exploring current and historical systems. It delves into various cryptosystems and cryptographic techniques, their operations, and provides hands-on experience with contemporary cryptographic technology.
Cyber Security Assessment and Management
This course offers an understanding of information security terminology, principles, and best practices, both locally and globally. It includes an overview of networking components, security vulnerabilities, and countermeasures through planning and administrative controls in an organization
AI for Cybersecurity
This course explores the convergence of AI and Cybersecurity. It delves into AI's role in advancing cybersecurity, teaches about machine learning for threat detection, and discusses the ethics of AI in security. With a blend of theory and practice, this course prepares participants to tackle contemporary security challenges using the latest AI and cybersecurity tools.
Computer Network Security
This course focuses on the introduction to Network Security, including foundations of networking, applying security functionality via protocols and controls, security architectures, and network security operations.
Incident Response and Recovery
This course provides an in-depth exploration of disaster recovery planning, encompassing strategies to prevent, detect, and recover from disruptions in information availability. It covers the formulation and implementation of Incident Response, Disaster Recovery, and Business Continuity plans. The course combines theoretical knowledge with hands-on experience in a simulated lab, equipping students with the skills to develop, test, and execute these plans effectively.
IoT Security
This course serves as an introduction to the Internet of Things (IoT), focusing on the core concepts underpinning IoT technologies and their applications, while also identifying security risks within IoT ecosystems. It explores effective strategies to minimize these vulnerabilities.
Cloud Security
This course teaches designing cloud-based solutions for data availability, confidentiality, and integrity. Topics include cloud service models, deployment methods, Identity And access Management strategies, auditing, threat mitigation, compliance, and hands-on in cloud environments.
Design and Development of Secure Software
This course covers secure software development throughout software development life cycle (SDLC), focusing on coding, technology, tools, and processes. It highlights the Defense in Depth principle and adapts security activities to Agile and DevSecOps practices.
EC-C Certification: CEH or NDE
Certified Ethical Hacker CEH v12 will teach you the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organization.
Blockchain Technology
This course covers the basics of blockchain technology, including its history, technical foundations like hashing and smart contracts, and platforms like Bitcoin and Ethereum. It also offers hands-on experience in setting up and working with various blockchain technologies.
Security and Privacy
This course focuses on secure data handling, understanding privacy principles, and managing privacy risks in datasets, aligned with current global best practices.
Digital Forensics + Certification
This course explores digital forensics, focusing on media analysis, data reconstruction, network forensics, and the legal aspects of digital data in criminal and civil litigation.
Thesis
The Master of Cybersecurity thesis allows learners to demonstrate their capability to establish a durable cybersecurity and information assurance program. The thesis project challenges learners to integrate skills and knowledge from all program domains into one project that addresses a significant real-world cybersecurity problem.
| Apply Now
|
Given limited capacity, MedTech admission criteria are highly selective.
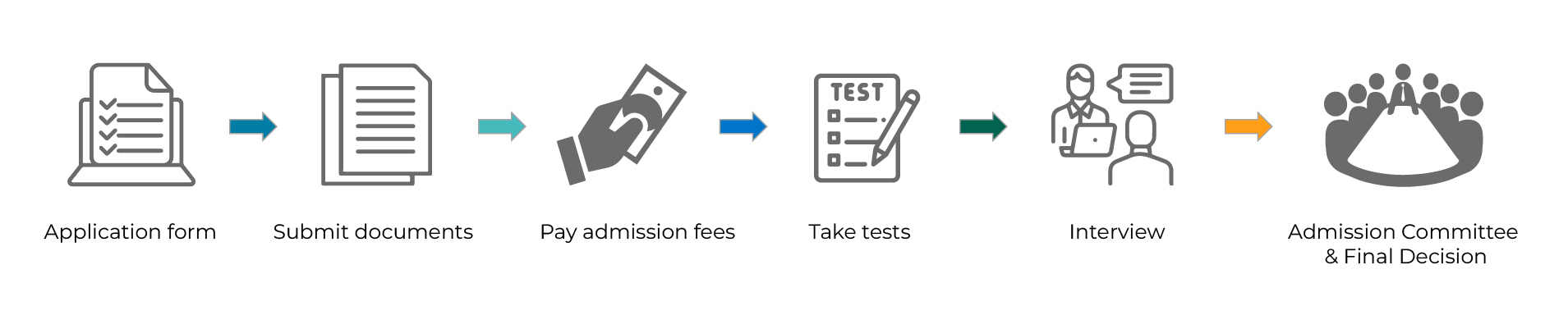
Admission requirements include:
Electrical and Computer Engineering, Electrical, and Telecommunication Engineering.
| Apply Now
|
Graduates of the Master degree program in Cyber Security will be prepared to work at IT and management consultancies and in service/product companies, and to pursuit a research career towards a PhD degree.
Exemplary positions for graduates with emphasis on services and business processes are: Security Analyst, Security Engineer or Architect, Security/IT Director or Manager, CISO/CSO, Systems Administrator, Network Architect or Engineer, Forensics Investigator, Auditor, Systems Engineer or Integrator.
 |
Hichem Kallel |
|
Professor Hichem Kallel is a distinguished expert in Electrical Engineering, specializing in Robotics, with a Ph.D. from Ohio State University, USA. Currently, he serves as the Dean of the Mediterranean School of Technology at Southern Mediterranean University, Tunisia. Dr. Kallel has an extensive industrial background, having held positions such as CEO of Golden Krispy's and managerial roles in the Poulina Group. He is renowned for his contributions to the fields of Robotics Kinematics, Dynamics Modeling and Control, Industrial Robotics, and Automation. Additionally, Dr. Kallel has made significant advancements in the study of Neural Networks, Artificial Intelligence, and Deep Learning.
|
|
|
|
|
 |
Imed Hammouda |
|
Dr. Imed Hammouda is currently Professor and Dean of the Mediterranean Institute of Technology (MedTech), South Mediterranean University, Tunisia. His academic interests include software development methods and tools, software ecosystems, open-source software, software architecture, and variability management. He has been the principal investigator of several research projects focused on software development, software ecosystems, and various open initiatives. He is the author of more than 100 academic articles and proceedings. Before joining MedTech, he was an Associate Professor of software engineering at Chalmers and the University of Gothenburg, Sweden where he acted as program director for the Software Engineering and Management bachelor program
|
|
|
|
|
 |
Ghassen Kilani |
|
Dr. Ghassen Kilani is an Assistant Professor of Computer Science and Cyber Security Coordinator at MedTech. He is an expert in Blockchain technology and Web 3 and has extensive knowledge of Cyber practices, information privacy, and Secure Communications. With a Ph.D. in Computer Science and a Master of Science in Information Assurance and Cyber Security, Ghassen is particularly interested in exploring the intersection of cyber security and emerging technologies such as Artificial Intelligence and IoT. He believes that staying ahead of the curve and anticipating new cyber threats is crucial in today's ever-evolving digital landscape.
|
|
|
|
|
 |
Darine Ameyed |
|
Dr. Darine Ameyed is a professional in human-aware intelligent technology, based in Montreal, Quebec, Canada. Her career highlights include her role as an Affiliate Professor at the University of Quebec in Chicoutimi and at the University of Sherbrooke. She has been working as an AI Lead Senior Research Advisory & Consultant at the Ministry of Cybersecurity in Quebec, focusing on AI implementation in the public sector and leading AI R&D projects. Additionally, she has been an advocate for smart, sustainable city policies and was an Associate Research Scientist at the Synchromedia Laboratory, specializing in AI, ambient intelligence, cognitive IoT, and blockchain for privacy and data security
|
|
|
|
|
 |
Jihen Ben Naceur |
|
Dr. Jihen Ben Naceur has got the Research Master’s Degree in Communication Systems in 2015, and the Ph.D. degree in Computer Science in 2020 from ENSI university jointly with cooperation with the university of UPEC(France). She is a researcher at CRISTAL Laboratory at ENSI and LISSI Research Center at university of UPEC in France. She is currently a cybersecurity postdoc at Medtech and the german compagny Sama partners business solutions. Her research areas of interest include Wireless Sensor Networks, Cognitive Radio Network, IoT applications, Artificial Intelligence, Blockchain, Cybersecurity, Information sharing, SDN and 5G.
|
|
|
|
|
 |
Abdeljalil Labed |
|
Dr. Abdeldjalil Labed is a computer scientist with a PhD in Intelligent Science and Systems from Macau University of Science and Technology. He specializes in cybersecurity, focusing on the development of intelligent intrusion detection systems. His expertise extends to various technical domains, including Blockchain, Cloud Computing, and Mobile App Development.
|
|
|
|
|
 |
Amina Mseddi |
|
Dr. Amina Mseddi has earned both her Master's and Ph.D. in Computer Science from the University of Quebec in Montreal. Additionally, she obtained an engineering degree specializing in Computer Networks and Telecommunication from INSAT. She is currently an Assistant Professor and Program Director at the Mediterranean Institute of Technology where she teaches distributed systems and cloud computing courses. Her research interests encompass cloud computing, edge computing, the Internet of Things (IoT), and Artificial Intelligence (AI).
|
|
|
|
|
 |
Salma Hamza |
|
Dr. Salma Hamza is currently an Assistant Professor at the Mediterranean Institute of Technology. she received her Ph.D. from Institut de recherche en Informatique et systèmes aléatoires in France in 2014. Before joining MedTech, she has been a research fellow at the University of Michigan Dearborn, USA, and a research engineer at Amadeus, France. Her research interests include software evolution, metrics, repositories, defect analysis as well as software engineering in general. She also worked on model-driven engineering, reverse engineering, refactoring of software using static analysis, and component-based software engineering.
|
|
|
|
|
 |
Fehimi Jaafer |
|
Dr. Fehmi Jaafar is an Associate Professor at Quebec University in Chicoutimi and Director of the Cyber Defense Research Chair. His prior roles include Researcher at the Computer Research Institute of Montreal and Affiliate Assistant Professor at Concordia University. He completed postdoctoral research at Queen’s University and Polytechnique Montreal. Dr. Fehmi specializes in cybersecurity, particularly in IoT, software system security and quality, and the application of machine learning in cybersecurity.
|
| Apply Now
|
In today's digital era, the cybersecurity field is rapidly expanding, presenting significant opportunities for those with the right certifications. As digital technologies become increasingly integral to businesses and cyber threats continue to rise, there is a growing demand for skilled cybersecurity experts.
Organizations are actively seeking professionals capable of managing and mitigating cyber risks. Acquiring a cybersecurity certification from EC-Council can help you bridge this skills gap and significantly advance your career. Our globally recognized certifications encompass key areas such as ethical hacking, network defense, and computer forensics, tailored to align with the most in-demand job roles in the industry.
Our certification programs are designed for individuals at all levels, from beginners starting their cybersecurity journey to seasoned professionals seeking to enhance their skills. By joining us, you gain access to comprehensive training in the latest security protocols and technologies, setting the stage for you to thrive in this vital and evolving field.
The International Council of E-Commerce Consultants, or EC-Council, stands as the world’s leading authority in cyber security certification. Operating in 145 countries, EC-Council has developed and owns esteemed certifications such as the Certified Ethical Hacker (C|EH), Computer Hacking Forensics Investigator (C|HFI), and the Certified Security Analyst (ECSA). Their programs have contributed to the training and certification of over 300,000 information security professionals globally. This has significantly influenced the cyber security landscape of numerous organizations around the world.
EC-Council is a member-based organization pivotal in certifying individuals in diverse e-business and information security skills. They are globally recognized for the creation of the flagship Certified Ethical Hacker (C|EH), Computer Hacking Forensics Investigator (C|HFI), and the EC-Council Certified Security Analyst (ECSA). Their programs have been endorsed by various government agencies, including the US Federal Government and the NSA. Furthermore, EC-Council’s credentials have achieved accreditation from the American National Standards Institute (ANSI), affirming their commitment to excellence in Cybersecurity training.
|
Course Description
Certified Ethical Hacker CEH v12 will teach you the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organization. Key Outcomes
|
|
Course Description
Certified Network Defender CND v2 provides a comprehensive approach to effectively deal with security issues in today’s modern network. Key Outcomes
|
|
Course Description
Computer hacking forensic investigation is the process of detecting hacking attacks and properly extracting evidence to report the crime and conduct audits to prevent future attacks. Key Outcomes
|
For More Details:
South Mediterranean University is the first and only CFA recognized University in Tunisia. Our Master program in Mana...
Marketing is a holistic approach that aims to assess market and business situations, analyze trends, identify and des...
Supply Chain and Operations Management is about planning, scheduling, managing, and controlling all the resources whi...
This specialization aims to prepare future Business Analysts and Managers to acquire, develop, and apply skills, know...
MSB-EADA Dual Degree program provides students with the opportunity to complete the MSB MBM degree and a Master’s fro...
MSB students interested in going to HEC have the opportunity to obtain a “Diplôme d'études supérieur spécialisé” (D.E...
Healthcare management may be of interest to someone who wants to contribute significantly to healthcare without havin...
It is a Part-time Master in Business Administration - Part-time MBA, with a focus on Artificial Intelligence.
ESC Clermont Business School has been recognized for the quality of its training, its diplomas and its support in ord...